Why consent management belongs at the core of customer experience
Consent management protects trust and reduces regulatory risk. It defines how an enterprise captures a person’s choices, stores the evidence, and enforces those choices across data flows, channels, and vendors. Strong consent management improves conversion because people understand what they agree to. Weak consent management creates friction, leaks data, and invites penalties. This article explains the consent lifecycle and shows how to connect it to access control and retention so leaders can ship compliant, customer-centred systems at scale.¹ ²
What is “consent” in a regulatory sense?
Regulators treat consent as a clear, informed, specific, and unambiguous signal from the person that authorises processing of their personal data for named purposes. Under the EU GDPR, consent must be freely given, specific, informed, and indicated by a clear affirmative action. The UK ICO echoes this definition, and the guidance sets conditions such as easy withdrawal, demonstrability, and separation from terms. Australia’s OAIC describes the elements as informed, voluntary, current, and specific, with capacity. These shared principles give you a common bar to design to, even if implementations vary by region.¹ ⁸ ¹ ⁰
How do you capture consent without losing the customer?
Design capture as a flow, not a pop-up. A consent capture flow collects purpose-by-purpose choices, explains consequences, and offers an equivalent path when a person declines. Build the capture experience on three primitives: purposes, legal bases, and processing activities. Purposes define why you process data, such as analytics or personalisation. Legal bases establish authority, such as consent or legitimate interests. Processing activities link systems, vendors, and data elements to each purpose. This structure lets you present clear options and minimises dark patterns. Use progressive disclosure to show detail on demand, and let people change their mind with one click. Capture should default to off for non-essential purposes and record the exact text, timestamp, and context.¹ ⁸
What does “consent storage” actually store?
Consent storage preserves evidence and makes it computable. Store a consent record with person identifier, purposes, legal basis, scope, timestamp, provenance, and expiry. Include the versioned policy text and UI snippet presented at the moment of capture so you can later demonstrate transparency. A standardised “consent receipt” makes the record portable and human-readable. The Kantara Consent Receipt specification defines a structured way to issue a receipt that a person can review or present elsewhere. Many teams store receipts in JSON, expose them via an API, and send a copy to the person’s email or portal. This pattern simplifies audits and supports cross-system enforcement.⁵ ¹³ ²¹
How is consent enforced at runtime across apps and vendors?
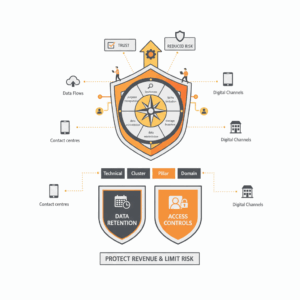
Enforcement binds consent to access decisions. Treat consent as a policy input to authorisation. At request time, the enforcement service checks whether the requested purpose matches the person’s current consent for that purpose and context. OAuth 2.0 provides the industry standard framework to issue tokens that carry scope. UMA 2.0 extends OAuth so a resource owner can set policies once and have a trusted authorisation server enforce them across clients. Use these protocols to propagate purpose-scoped, time-bound access downstream. A vendor or microservice reads the token, verifies scope, and serves or denies data accordingly. This gives you a reliable way to translate a person’s choices into live access control.⁷ ¹⁵ ⁶ ¹⁴ ²² ²³
How do banners and adtech handle transparency and consent?
The online advertising ecosystem uses a shared signalling approach to transmit choices. IAB Europe’s Transparency and Consent Framework defines policies and technical specifications so publishers and vendors can read a consistent “TC string” that expresses purposes and features. TCF seeks to operationalise GDPR and ePrivacy requirements in this specific context. For teams with advertising or CMP requirements, aligning to TCF reduces vendor friction and improves demonstrability of choices at scale. Ensure your CMP can map internal purposes to TCF purposes and keep pace with updates and rulings.¹² ⁴ ²⁰
How do you connect consent to retention and data minimisation?
Retention and minimisation reduce risk and respect customers. Treat retention as part of the consent contract. When you collect personal data under a consent legal basis, attach a retention policy to each purpose. The policy defines how long you keep the data and what happens at expiry. Store the policy identifier on the consent record and enforce it in the data platform. That enforcement includes scheduled deletion, aggregation, or tokenisation. Align collection to “necessary for purpose” tests under Australian APP 3 and similar principles in other regimes. This keeps the footprint small and the narrative honest.¹⁷ ¹
What frameworks guide a mature consent program?
Several frameworks provide structure and common language. The NIST Privacy Framework helps organisations identify and manage privacy risk by mapping business objectives to controls, including consent and preference management. ISO/IEC 27701 extends ISO 27001 to define a Privacy Information Management System and includes guidance for consent records and roles for PII controllers and processors. Together, they offer a control-based path to scale practices across business units, systems, and vendors.³ ¹⁰ ²
How do you measure consent management that actually works?
Measure what customers feel and what systems prove. Track opt-in rates by purpose, consent change rates, withdrawal latency, and downstream enforcement failures. Monitor the percentage of data assets with mapped purposes, legal bases, and retention policies. Include operational metrics such as token scope violations, orphaned data after withdrawal, and audit response times. Tie these metrics to customer outcomes like conversion and churn to show the CX impact of clarity and control. Use NIST-aligned privacy risk registers to connect measurement to risk appetite and remediation plans.³
What is the step-by-step implementation path?
Leaders can implement consent management in nine steps. The sequence aligns design, legal authority, and technical enforcement so you avoid rework.
Document purposes and processing activities. Build a canonical catalogue. Map data elements, systems, and vendors to each purpose. Mark legal bases by jurisdiction and business unit. This becomes the source for UI content and enforcement policies.¹ ⁸
Design the capture experience for clarity. Write short, active, non-bundled language for each purpose. Provide equal prominence to accept and decline. Offer a path to continue without non-essential processing. Localise content with legal sign-off.¹ ⁸
Select a consent receipt format. Implement JSON receipts that follow the Kantara model and include policy version, timestamp, and provenance. Expose a receipt endpoint in the customer portal and via API.⁵ ¹³
Deploy a central consent API. Create endpoints to create, read, update, and withdraw consent by person and purpose. Emit events on change. Store evidence with cryptographic integrity and audit trails. Connect the API to the identity provider for consistent person resolution.²
Bind consent to authorisation. Use OAuth 2.0 as the token service and encode purpose scopes in tokens. Where resource-owner policy is needed across domains, implement UMA 2.0 so a central authorisation server can evaluate consent and policy at runtime.⁷ ¹⁵ ⁶
Instrument downstream enforcement. Require services and vendors to verify tokens and check scope before serving data. For batch analytics, build query guards that filter data sets by current consent. Log decisions for audit and incident response.²²
Attach retention to purposes. For each purpose, define retention duration and action at expiry. Tag data at ingestion with purpose and retention. Run automated jobs to expire data and produce deletion certificates. Align to APP 3 and similar minimisation principles.¹⁷
Operationalise transparency and adtech signals. If you participate in programmatic ads, integrate a CMP that supports IAB TCF and keeps TC strings current. Ensure internal purposes map to TCF purposes and that withdrawals propagate.¹² ⁴ ²⁰
Adopt a control framework. Map your processes to NIST Privacy Framework functions and ISO/IEC 27701 control families. Use these frameworks to govern change, test controls, and report maturity to executives and auditors.³ ² ¹⁰
How does this protect the business and the brand?
This approach improves compliance and experience together. Clear capture reduces friction and prompts informed acceptance. Strong storage creates evidence you can present in audits. Runtime enforcement prevents accidental misuse and limits blast radius during incidents. Purpose-based retention keeps the estate lean and lowers operational risk. By building on open standards and recognised frameworks, teams reduce integration effort and improve portability across regions and vendors. The result is a customer experience that earns trust and a control environment that scales.³ ² ¹⁰ ¹
FAQ
What is valid consent under GDPR and how should we present it in the UI?
Valid consent is freely given, specific, informed, and indicated by a clear affirmative action. Present purpose-level choices, avoid bundling, and make withdrawal as easy as giving consent.¹ ⁸
How should we store a consent record to satisfy audits?
Store a structured record with person identifier, purpose, legal basis, timestamp, provenance, and policy version, and issue a human-readable consent receipt based on the Kantara specification.⁵ ¹³
Which standards help connect consent to access control?
Use OAuth 2.0 to issue purpose-scoped tokens and consider UMA 2.0 when you need resource-owner policies enforced across domains and clients.⁷ ⁶ ¹⁵
Why link consent to retention and minimisation in data platforms?
Linking consent to retention ensures data is kept only as long as necessary for the agreed purpose and supports obligations like Australia’s APP 3 minimisation principle.¹⁷ ¹
Which frameworks guide a scalable consent management program?
Adopt the NIST Privacy Framework to manage privacy risk and ISO/IEC 27701 to implement a Privacy Information Management System across controllers and processors.³ ² ¹⁰
How does the IAB Transparency and Consent Framework fit into CMP implementations?
The IAB TCF provides shared policies and technical specifications for transmitting choices across advertising vendors, reducing integration effort and helping operationalise GDPR and ePrivacy requirements.¹² ⁴ ²⁰
Who benefits from consent receipts and why?
Customers gain transparency and portability, while organisations gain demonstrable evidence of lawful processing, improving audit readiness and customer trust.⁵ ¹³
Sources
Guidelines 05/2020 on consent under Regulation 2016/679 (GDPR), European Data Protection Board, 2020, EDPB. https://www.edpb.europa.eu/sites/default/files/files/file1/edpb_guidelines_202005_consent_en.pdf
ISO/IEC 27701:2019 Security techniques — Extension to ISO/IEC 27001 and 27002 for privacy information management, ISO, 2019, International Organization for Standardization. https://www.iso.org/standard/71670.html
NIST Privacy Framework, National Institute of Standards and Technology, 2020, NIST. https://www.nist.gov/privacy-framework
IAB Europe Transparency & Consent Framework Policies, IAB Europe, 2025, IAB Europe. https://iabeurope.eu/iab-europe-transparency-consent-framework-policies/
Consent Receipt Specification v1.1.0, Kantara Initiative, 2019 updated 2024, Kantara. https://kantarainitiative.org/download/consent-receipt-specification/
User-Managed Access (UMA) 2.0 Grant for OAuth 2.0 Authorization, Kantara Initiative, 2018, Kantara. https://docs.kantarainitiative.org/uma/wg/rec-oauth-uma-grant-2.0.html
RFC 6749: The OAuth 2.0 Authorization Framework, IETF, 2012, IETF RFC Editor. https://www.rfc-editor.org/info/rfc6749
What is valid consent?, Information Commissioner’s Office, 2023, ICO. https://ico.org.uk/for-organisations/uk-gdpr-guidance-and-resources/lawful-basis/consent/what-is-valid-consent/
Consent to the handling of personal information, Office of the Australian Information Commissioner, 2022, OAIC. https://www.oaic.gov.au/privacy/your-privacy-rights/your-personal-information/consent-to-the-handling-of-personal-information
ISO/IEC 27701 Overview, ISO, 2025, International Organization for Standardization. https://www.iso.org/standard/27701
Chapter 3: APP 3 — Collection of solicited personal information, Office of the Australian Information Commissioner, 2019, OAIC. https://www.oaic.gov.au/privacy/australian-privacy-principles/australian-privacy-principles-guidelines/chapter-3-app-3-collection-of-solicited-personal-information
Transparency & Consent Framework (TCF) — What is the TCF?, IAB Europe, 2024, IAB Europe. https://iabeurope.eu/transparency-consent-framework/
Consent Receipt Specification (Archived Wiki), Kantara Initiative, 2017, Kantara. https://kantara.atlassian.net/wiki/spaces/archive/pages/3508790/Consent%2BReceipt%2BSpecification
PT-4 Consent (NIST SP 800-53 Rev. 5), NIST CSF Tools reference, 2021, CSF.tools. https://csf.tools/reference/nist-sp-800-53/r5/pt/pt-4/
OAuth 2.0 Overview, OAuth.net, 2024, The OAuth Community. https://oauth.net/2/
Transparency & Consent Framework — Legal Update (May 2025), IAB Australia, 2025, IAB Australia. https://iabaustralia.com.au/guideline/transparency-consent-framework-tcf-legal-update-may-2025/