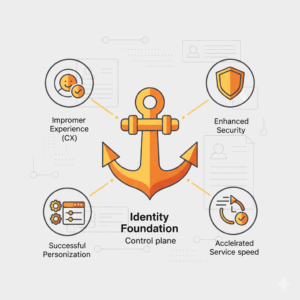
Why do identity foundations matter to CX and service outcomes?
Identity anchors every digital interaction. Strong identity foundations let customers authenticate quickly, employees work securely, and systems personalise without breaching trust. Identity reduces friction, cuts fraud, and accelerates service speed. Leaders use identity to connect profiles, preferences, and consent to measurable outcomes. Identity becomes the control plane for experience, security, and data governance when programs align policy, platform, and operating rhythm.¹
What is an “identity foundation” in practical terms?
An identity foundation is the minimal viable set of capabilities that prove, govern, and use identities across the enterprise. This foundation spans people, non-human agents, devices, and services. It includes identity proofing, authentication, authorisation, lifecycle management, consent, and audit. A practical foundation implements assurance levels, phishing-resistant MFA, and federated single sign-on. It also implements role and attribute models that align to business policy. Standards such as NIST SP 800-63 provide the scaffolding for assurance and federation, while Zero Trust positions identity as the primary control point.¹² (NIST)
How should executives frame the problem statement?
Executives should frame identity as both risk and growth. Weak identity increases account takeover, privacy incidents, and operational drag. Strong identity reduces handling time, simplifies channel switching, and improves self-service conversion. Leaders should define the stakes in customer language: faster onboarding, fewer password resets, cleaner data for insights, and trustworthy consent. The problem statement should quantify baseline friction, fraud, and rework. The statement should align identity investments to specific CX and service metrics, not just security posture.²
What does a fit-for-purpose identity rollout look like?
A fit-for-purpose rollout moves in controlled waves. Teams minimise dependencies and maximise learning in each wave. Wave 1 secures administrators and privileged access. Wave 2 lifts assurance and MFA for workforce identities. Wave 3 modernises customer login and consent with progressive profiling. Wave 4 expands governance to non-human identities such as service accounts and automations. Each wave ends with measurable outcomes: adoption, step-up rates, and risk reduction. Zero Trust playbooks provide a safe sequence and shared language for each pillar.²⁵ (Microsoft Learn)
What policies do you need on day one?
Programs should codify five policies on day one. First, adopt an identity assurance policy that maps use cases to authentication strength. Second, adopt a role and attribute policy that clarifies who assigns roles, who approves access, and how attributes flow. Third, adopt a consent and purpose-limitation policy that binds data use to explicit user permission. Fourth, adopt a lifecycle policy for joiners, movers, leavers, and non-human identities. Fifth, adopt an audit and exception policy that documents break-glass access and monitoring. NIST, ISO, and local privacy principles support these policy definitions and create a durable compliance base.¹³⁴ (NIST)
How do local regulations shape identity design in Australia?
Australian Privacy Principles govern how organisations collect, use, and disclose personal information. Programs must implement consent capture, data minimisation, access and correction rights, and transparency. Technical controls should make compliance the default, not an afterthought. Design should ensure purpose limitation, retention rules, and traceability for consent changes. CX leaders should sequence consent prompts to support journey momentum rather than stall conversion. The APPs are principles-based, so enterprise policy should translate them into control requirements that platforms can enforce.³ (OAIC)
What core mechanisms make the foundation durable?
Strong mechanisms make identity reliable at scale. Identity proofing establishes who is on the other end and sets assurance baselines. Phishing-resistant MFA enforces strong authentication without training users to accept prompts blindly. Federation reduces password sprawl and supports partner ecosystems. Authorisation uses roles and attributes to apply least privilege consistently. Lifecycle automation ensures joiners receive the right access on day one and leavers lose access on day zero. Logging, analytics, and risk engines tie these mechanisms together to adapt in real time.¹²⁶
How do you compare RBAC, ABAC, and PBAC in the real world?
Role-based access control works well for stable job functions. Attribute-based access control excels when context matters, such as location or device posture. Policy-based access control abstracts both into human-readable policies and centralises decisions. Most enterprises start with RBAC, enrich with attributes for context, and graduate to policies for scale. Identity governance systems provide the approvals, certifications, and access reviews across each model to keep drift under control. Governance makes entitlements explainable and provable to auditors and business owners.⁷
Where do non-human and AI agent identities fit?
Non-human identities already outnumber human users in many environments. Service accounts, APIs, bots, and AI agents must follow the same lifecycle rigor as people. Programs should mint identities per workload, avoid shared secrets, and enforce least privilege with short-lived credentials. Teams should bind any agent to an accountable human owner. Identity catalogs should tag agents with clear purpose and expiry dates. This approach reduces shadow access and makes AI systems auditable. It also keeps data foundations clean by separating human profiles from machine profiles for accurate analytics.⁶
How do you measure maturity without creating bureaucracy?
Leaders should measure maturity with a concise scorecard. The scorecard should track adoption of phishing-resistant MFA, percentage of apps federated, time to provision and deprovision, certification completion, and orphaned accounts. It should track consent coverage and the percentage of events tied to a known identity. It should measure user-perceived friction in seconds and steps, not pages and policies. Programs should target quarterly improvements and publish trend lines. Identity should earn its keep with visible, compounding gains to CX and service metrics.²⁶⁷
What operating model sustains momentum after go-live?
A sustainable operating model blends platform, policy, and people. Product owners treat identity as a product with a backlog, roadmap, and service levels. Security architects define assurance, guardrails, and threat models. CX teams co-design flows, copy, and recovery paths. Data stewards define profile schemas, quality rules, and consent taxonomies. Procurement aligns vendor access with contracts and risk. Internal comms and training treat identity change as behaviour change. Governance operates on a cadence with quarterly access reviews, break-glass tests, and risk drills.²⁷
How do you de-risk technology choices?
De-risk choices by aligning requirements to reference architectures and published standards. Teams should evaluate platforms for phishing-resistant MFA, policy-driven access, lifecycle automation, and analytics. They should review identity governance features for access reviews, segregation-of-duties, and birthright access. They should confirm roadmap fit for non-human identities and secrets automation. They should also stress-test vendor incident response and hardening practices using recent public learnings. The Okta incident illustrates the value of mandatory admin MFA and constrained support access after lessons learned.⁶⁸ (Axios)
What is the simplest rollout sequence that works in most enterprises?
Start by securing the blast radius. Protect administrators and privileged roles with phishing-resistant MFA and conditional access. Inventory apps and federate the top thirty by usage to cut password resets and ticket volume. Switch workforce to modern authenticators while preserving break-glass paths. Introduce governance with quarterly certifications for high-risk roles. Expand to customer identity with social and passkey options, progressive profiling, and consent logging. Bring non-human identities into lifecycle automation and secrets rotation. Close the loop with dashboards that show CX gains and risk reduction in one view.¹²⁶
How do you translate identity into measurable business impact?
Tie identity to business KPIs and publish the wins. Measure lower abandonment from passkeys versus passwords. Track reduction in average handle time after SSO. Quantify fewer fraud cases after step-up authentication in risky flows. Show faster partner onboarding with federation. Convert privacy compliance into trust signals on consent and preference pages. Identity foundations create a flywheel for CX and service. That flywheel spins faster when metrics prove value to executives, risk committees, and frontline teams alike.²³
Implementation Checklist: the executive short list
Establish policy baselines for assurance, roles, consent, lifecycle, and audit.¹³⁴
Prioritise administrator and privileged access with phishing-resistant MFA.²⁶
Federate your top apps and retire redundant passwords.²
Operationalise identity governance with access reviews and SoD rules.⁷
Automate joiner, mover, leaver flows for people and agents.²⁶
Instrument journeys and publish CX and risk metrics every quarter.²
Run playbooks for incident response, break-glass, and consent revocation.²³⁶
FAQ
What is an identity foundation and why does it matter for CX at Customer Science clients?
An identity foundation is the minimal viable capability set to prove, govern, and use identities across customers, employees, and non-human agents. It improves onboarding speed, reduces friction, and enables consent-driven personalisation, which lifts customer experience and service performance.¹²
How should Australian organisations align identity with the Australian Privacy Principles (APPs)?
Organisations should embed consent, purpose limitation, data minimisation, access rights, and transparency into identity flows. The APPs are principles-based, so translate them into platform controls such as consent logging, retention policies, and auditable user access.³
Which standards guide assurance levels, MFA strength, and federation?
NIST SP 800-63 outlines identity proofing, authenticator assurance, and federation patterns. It provides a risk-based method to match authentication strength to transaction risk.¹
How does Zero Trust change identity rollout priorities?
Zero Trust puts identity at the centre of access decisions. Programs first secure administrator accounts, enforce phishing-resistant MFA, and apply least privilege with continuous evaluation. Microsoft’s deployment guidance offers practical checklists and sequences.²
What roles and systems deliver identity governance and administration (IGA)?
IGA tools manage the identity lifecycle, govern entitlements, and run access reviews and certifications. They aggregate access data, detect segregation-of-duties conflicts, and provide auditable controls for regulators and business owners.⁷
Which best practices reduce risk during rollout without hurting UX?
Use phishing-resistant MFA, federate priority apps, adopt role and attribute models, automate lifecycle for joiners and leavers, and design consent prompts that support journey momentum. Okta and similar providers document these practices in accessible guides.⁶
Who owns non-human and AI agent identities in modern data foundations?
Each agent identity should have an accountable human owner. Assign purpose, scopes, and expiry, and manage credentials with rotation and short lifetimes. Treat agents like workforce identities in lifecycle, governance, and audit.⁶
Sources
NIST SP 800-63-4: Digital Identity Guidelines — Grassi, P., Lefkovitz, N., et al. (2025), NIST. https://www.nist.gov/publications/nist-sp-800-63-4-digital-identity-guidelines (NIST)
Identity, the first pillar of a Zero Trust security architecture — Microsoft Learn Authors (2024), Microsoft. https://learn.microsoft.com/en-us/security/zero-trust/deploy/identity (Microsoft Learn)
Australian Privacy Principles quick reference — Office of the Australian Information Commissioner (OAIC) (2025). https://www.oaic.gov.au/privacy/australian-privacy-principles/australian-privacy-principles-quick-reference (OAIC)
ISO/IEC 24760-1:2019 IT Security and Privacy — A framework for identity management — ISO (2019, updated 2025 catalog). https://www.iso.org/standard/77582.html (ISO)
A Practical Guide to a Zero Trust Implementation — Forrester Research (2021). https://4719eaee91034be722d8-c86a406a93c55de2464febd03debd4f0.ssl.cf1.rackcdn.com/A_Practical_Guide_To_A_Zero_Trust_Implementation.pdf (Rackcdn)
Identity and Access Management Best Practices for Enhanced Security — Okta (2025). https://www.okta.com/identity-101/identity-and-access-management-best-practices-for-enhanced-security/ (Okta)
Identity Governance and Administration definition — Gartner Peer Insights Glossary (2025). https://www.gartner.com/reviews/market/identity-governance-administration (Gartner)
Okta introduces new security plan after October cyberattack — D. McCabe (2024), Axios. https://www.axios.com/2024/02/28/okta-security-plan-cyberattack (Axios)