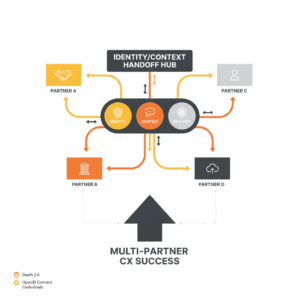
Why does identity and context handoff decide multi-partner CX success?
Leaders run multi-partner ecosystems to meet customer expectations, but identity breakdowns create friction that customers feel instantly. Identity and context handoff is the controlled transfer of who the customer is and what is happening in their journey between parties. Good handoff preserves authentication, authorisation, and real-time context so the next team can act without repeating questions or revalidating details. Standards such as OAuth 2.0 define scoped access to resources, not password sharing, which is the foundation for safe delegation between systems.¹ OpenID Connect extends OAuth to assert who the user is through signed ID tokens and claims so partners receive verifiable identity signals.² When leaders treat identity and context as first-class products, ecosystems scale without sacrificing trust. NIST’s Digital Identity Guidelines formalise levels of assurance for proofing and authentication so leaders can match controls to risk while keeping experience smooth.³
What do we mean by “identity” and “context” in a partner flow?
Teams often conflate identity with a username. Identity is the set of attributes that uniquely represent a person or organisation in a digital system. Authentication proves control of authenticators, while authorisation governs what the subject can do.³ Context is the time-bound state that gives meaning to actions. Examples include active case, product entitlements, channel, device posture, and consent status. Context must be fresh, purpose-limited, and auditable. The data minimisation principle under GDPR sets the tone: collect only what is adequate, relevant, and limited to what is necessary for the stated purpose.⁶ Purpose limitation protects customers and reduces liability. Practically, identity flows carry stable identifiers and signed assertions. Context flows carry ephemeral signals such as session risk, recent transactions, or a handoff reason. Together they enable a partner to continue a journey step without asking customers to start again.
How do standards enable secure, low-friction handoff?
Executives pick open standards to reduce vendor lock-in and increase interoperability across partners. OAuth 2.0 supplies access tokens with scopes that describe permitted APIs and durations.¹ OpenID Connect adds ID tokens that carry claims like subject, issuer, audience, and authentication time, which let receivers verify identity and recency.² Verifiable Credentials from W3C introduce a model for portable, cryptographically verifiable attestations issued by trusted parties and presented by holders to verifiers. These credentials move facts such as age, license, or membership across partners without centralising all data in one hub.⁴ Zero Trust Architecture from NIST reinforces that networks should grant no implicit trust. Every request is strongly authenticated, explicitly authorised, and continuously validated, regardless of originating network.⁵ Combined, these standards let ecosystems hand off identity and context with strong assurance while keeping the interaction fast and predictable.
Where do Australian regulations shape design choices?
Australian ecosystems run under the Consumer Data Right, which enables accredited third parties to receive consumer-authorised data from data holders in banking, energy, and more.⁷ The regime requires explicit consent, standardised data formats, and strong accreditation controls. The model creates clear expectations for identity and consent handoff between holders and accredited recipients. Penalties for inaccurate or poor data quality are real. In June 2025, National Australia Bank paid an infringement penalty related to CDR rule breaches tied to inaccurate disclosure of credit limit data to CDR providers, which impacted downstream customer decisions.⁹ This example highlights that identity and context handoff is not only a security topic. It is an experience quality and compliance topic. By designing for accurate, timely, and purpose-bound handoffs, leaders protect customers and preserve the promise of open data ecosystems.⁷ ⁹
What good looks like: the five design moves for partner handoff
Leaders standardise the identity backbone before scaling partnerships. First, define a single subject model with unique, non-recycled identifiers mapped across systems. Second, use OAuth 2.0 with short-lived access tokens and refresh tokens, plus token binding where supported, to limit misuse.¹ Third, implement OpenID Connect for authentication and propagate ID tokens with explicit audiences and nonce checks to defend against replay.² Fourth, treat consents as first-class context objects with clear purposes, durations, and revocation endpoints. Fifth, ship a Zero Trust posture that evaluates device, network, and behaviour risk at each hop, not just the edge.⁵ These moves let partners receive only what they need and no more, aligned with data minimisation.⁶ When leaders adopt this pattern, customers move across brands without repeated identity proofing, agents gain immediate context, and audit trails remain clean.
How do we orchestrate the actual handoff end-to-end?
Architects align on a journey-centric sequence. The initiating partner authenticates the customer using OpenID Connect and issues an ID token and an OAuth access token scoped to the next step’s API set.² The orchestrator records the handoff reason, the consent reference, the session risk posture, and a correlation ID. The receiving partner validates issuer, signature, audience, timestamps, and consent scope before exchanging the access token for contextual data through standard APIs.¹ The receiver renders the next action with minimal re-authentication, except where risk signals require a step-up.³ The system streams event telemetry back to the orchestrator for SLA tracking and experience analytics. If a partner cannot accept standards, the orchestrator uses a translation facade but maintains the same consent ledger and correlation logic. This approach keeps the ecosystem consistent even as individual partners mature at different speeds.
Which patterns fit common partner use cases?
Contact centre to field partner handoff benefits from a “Claim-plus-Context” pattern. The centre issues a signed claim that the caller completed verification at a defined assurance level along with a context object that holds case, address, and narrow entitlements.³ ⁵ Retail marketplace to finance partner handoff suits a “Consent-anchored Token Exchange” pattern. The marketplace sends a consent reference and exchanges partner-specific access tokens through OAuth, reducing exposure of raw personal data.¹ Omnichannel support to logistics partner uses a “Just-in-Time Attribute Retrieval” pattern. The logistics provider receives only delivery attributes at the moment of action, not the entire customer profile, which aligns with minimisation.⁶ Where regulatory data portability applies, a “Verifiable Credential Presentation” pattern allows the customer to present a credential issued by the original provider to the new provider without re-proofing.⁴ Each pattern limits data and accelerates time to value.
How should leaders measure the quality of handoff?
Executives manage what they can see. Strong programs instrument experience and control metrics together. Experience metrics include repeat-authentication rate across partners, average seconds to first actionable screen post-handoff, agent repeat question rate, and abandonment during partner transitions. Control metrics include token validation failure rate, consent mismatch rate, context staleness defects, and unauthorised data attribute access attempts. Programs should map these to assurance levels defined in NIST SP 800-63 so that stronger controls align with higher-risk journeys.³ Zero Trust guidance also encourages continuous evaluation, so leaders track policy decisions per request and the percentage of requests requiring step-up authentication.⁵ Finally, compliance metrics such as data minimisation conformance and CDR data quality defect rate matter in Australia.⁶ ⁷ Measurable handoff quality turns identity into a growth enabler rather than a compliance tax.
What are the main risks and how do we mitigate them?
Ecosystems face replay, token theft, linkability, and context drift. Replay attacks occur when tokens lack nonce or proper audience binding. OpenID Connect and strict audience checks reduce this risk.² Token theft surfaces when access tokens are long-lived or stored insecurely. Short lifetimes, sender-constrained tokens, and proof-of-possession mitigate exposure.¹ Linkability rises when stable identifiers or excessive attributes travel between partners. Use pairwise identifiers and minimal attribute sets to limit cross-partner correlation, aligning with GDPR principles.⁶ Context drift happens when stale or inconsistent case data follows the customer. Mitigate with time-to-live on context objects, versioned schemas, and event-driven updates. Zero Trust reminds teams to verify explicitly and continuously at every hop, so risk signals can trigger step-up without breaking the journey.⁵ These mitigations keep velocity high while reducing blast radius.
What are the practical next steps for a CX transformation lead?
Executives can act in ninety days. Stand up an identity reference architecture that names the subject model, assurance levels, token standards, and consent policies. Map top three partner journeys and instrument the handoff metrics from the prior section. Draft and sign a partner-to-partner operating agreement covering token formats, consent handling, incident response, and audit log availability. Align legal terms with CDR and GDPR principles where applicable.⁷ ⁶ Run a controlled pilot with one partner using short-lived tokens, ID tokens with pairwise identifiers, and a consent ledger. Validate measures weekly. Adopt W3C Verifiable Credentials where customers benefit from portable proofs such as eligibility or license.⁴ Close with a board-level review of outcomes and a plan to scale to additional partners. This cadence establishes repeatable identity and context handoff as a core capability rather than a one-off integration.
FAQ
What is identity and context handoff across partners?
Identity and context handoff is the controlled transfer of who the customer is and what is happening in their journey between separate organisations, using standards such as OAuth 2.0 for scoped access and OpenID Connect for authentication signals.¹ ²
How does Zero Trust change partner integrations?
Zero Trust removes implicit trust in networks and requires continuous verification of identity, device, and policy at each request, which improves the safety of cross-partner handoffs without adding unnecessary friction for customers.⁵
Which standards should Australian CX leaders prioritise first?
Start with OAuth 2.0 for authorisation, OpenID Connect for authentication, and the CDR data standards for accredited data sharing. Add NIST SP 800-63 alignment for assurance and W3C Verifiable Credentials for portable proofs where relevant.¹ ² ³ ⁴ ⁷
Why does data minimisation matter in partner journeys?
Data minimisation reduces risk and improves trust by sending only the attributes required for a specific purpose. This aligns with GDPR principles and lowers liability during cross-partner context transfers.⁶
Who governs assurance levels and proofing practices?
NIST SP 800-63 provides guidance on identity proofing, authentication, federation, and assurance levels that organisations can adopt to calibrate controls to journey risk.³
What risks should we watch during handoff?
Key risks include token replay, token theft, linkability through stable identifiers, and context drift from stale state. Controls include nonce and audience checks, short-lived sender-constrained tokens, pairwise identifiers, and time-boxed context with event updates.¹ ² ⁵
Which compliance regimes affect Australian partner ecosystems?
The Consumer Data Right sets accreditation, consent, and data quality rules for data sharing. Breaches can lead to penalties, as shown by the 2025 infringement penalty paid by National Australia Bank for CDR rule breaches.⁷ ⁹
Sources
RFC 6749: The OAuth 2.0 Authorization Framework. D. Hardt. 2012. IETF. https://www.rfc-editor.org/rfc/rfc6749
OpenID Connect Core 1.0. N. Sakimura, J. Bradley, M. Jones, B. de Medeiros, C. Mortimore. 2014. OpenID Foundation. https://openid.net/specs/openid-connect-core-1_0.html
Digital Identity Guidelines (SP 800-63-3). P. Grassi, M. Garcia, J. Fenton. 2017. NIST. https://pages.nist.gov/800-63-3/sp800-63-3.html
Verifiable Credentials Data Model v2.0. W3C Working Group. 2024. W3C. https://www.w3.org/TR/vc-data-model-2.0/
Zero Trust Architecture (SP 800-207). S. Rose, O. Borchert, S. Mitchell, S. Connelly. 2020. NIST. https://csrc.nist.gov/pubs/sp/800/207/final
UK GDPR Article 5(1)(c) Data minimisation. Information Commissioner’s Office. 2023. ICO. https://ico.org.uk/for-organisations/uk-gdpr-guidance-and-resources/data-protection-principles/a-guide-to-the-data-protection-principles/data-minimisation/
Data Standards – Consumer Data Right. Data Standards Body. 2023. Australian Government. https://dsb.gov.au/consumer-data-right/data-standards
Regulation (EU) 2016/679 Article 5: Principles relating to processing of personal data. European Union. 2016. legislation.gov.uk. https://www.legislation.gov.uk/eur/2016/679/article/5
Australia’s NAB pays A$751,200 penalty on breaches of Consumer Data Right rules. Reuters Staff. 2025. Reuters. https://www.reuters.com/sustainability/nab-pays-over-488800-penalty-over-breaches-consumer-data-rights-rules-2025-06-18/